| |
|
|
|
|
|
BestCrypt architecture details |
This section describes main modules of the BestCrypt system and provides a brief guide to the system functionality. The following figure shows the main modules of the BestCrypt:
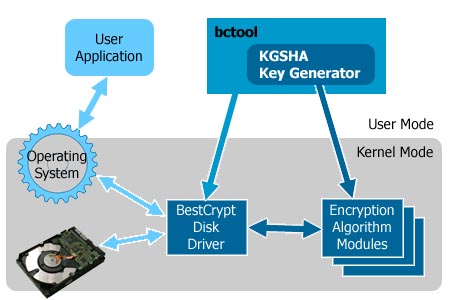 |
| Figure 1. |
As the figure above shows, some modules of the BestCrypt are implemented as user-level application: bctool utility with KGSHA Key Generator. Other modules (the BestCrypt Disk driver, Encryption Algorithm driver(s)) are the drivers running inside the operating system (Kernel mode drivers). Implementation of some modules as low-level system drivers allows BestCrypt to:
- create its own virtual drives that are native for the operating system;
- make all encryption operations on the fly, i.e. transparently for a user;
- get the operating system support for virtual drives - for example, caching mechanism helps BestCrypt virtual drives to work with a good performance.
Let's discover how BestCrypt works when user requests some operation with containeg, for example, mount:
-
BestCrypt's user application sends request to the Key Generation Module -
"get password for container and return encryption key handle for container
file".
Encryption key handle is just an identifier for encryption key data that is stored only inside Encryption Algorithm driver in a locked (non-swappable) memory. Encryption key data cannot be retrieved from the driver. There are not any ways to restore encryption key data from the key handle. - The Key Generator receives request "to get password for the container" together with a block of data being passed to BestCrypt Control Panel with the header of the file-container. The block of data allows the Key Generation Module to verify the password, extract the encryption key and convey the encryption key data to the Encryption Algorithm module.
- When the Key Generator receives the request from the BestCrypt application, it prompts the user to enter password. If the password is considered correct, the module passes encryption key data (for example, 256 bits for the GOST encryption algorithm) to the Encryption Algorithm module and clears all the memory reserved for temporary storage of the data related to the encryption key. The Encryption Algorithm module returns the key handle for the encryption key. Now the Key Generator has finished its job and returns the key handle to the BestCrypt application. Since that, the encryption key is stored only in the Encryption Algorithm module. The memory for the encryption key storage is locked, so the data cannot be swapped to the operating system swap file (and therefore be discovered there by a malefactor). Interface to the Encryption Algorithm module is designed so that it is impossible to get information from the Encryption module about the memory where the encryption key is stored.
- If the user enters the correct password and the Key Generator returns the valid key handle, the BestCrypt application generates a request package which contains the file name of the container and the key handle. The request is sent to the BestCrypt Disk Driver to create new virtual drive and associate it with the container file.
- After successful virtual disk creation BestCrypt application issues system call to mount it at requested mountpoint and protects it from accidental unmount.
- The BestCrypt Disk Driver owns a virtual drive, and as soon as the operating system needs to exchange data with the virtual drive, the data to be read or written by the driver find themselves in the container file. The Disk driver cannot access encryption key data directly, so when it is necessary to decrypt (encrypt) data from the file-container, the driver calls the Encryption Algorithm driver to perform the operation using the key handle which corresponds to the container file.
The BestCrypt is able to use more than one Encryption Algorithm Modules. For example, the current version of the BestCrypt has ten algorithms available, including Rijndael, Blowfish, Twofish and GOST28147-89.
This document, together with source codes of the Key Generation and Encryption Algorithm modules, may be helpful for third-party developers to create their own modules for the BestCrypt. Besides, there is a possibility to replace the BestCrypt modules with custom-designed modules.
| |
|
|
|
|
|