Featured News
|
Harry Potter Alert -- Muggles take over Insecure.Org!
|
|---|

|
June 21 -- Our web servers are struggling to cope with the
load after a hacker posted what he claimed were spoilers for the
upcoming book Harry
Potter and the Deathly Hallows. These were posted to a mailing list (fulldisclosure) which we automatically archive, and we have no idea if they are true or not. Reading
them could affect your enjoyment of the book! So you might prefer to
pre-order
the book and be patient until July 21 release date instead.
But if you really want the (possibly false) spoilers, here they
are. Our bandwidth graph shows that Harry Potter is a little more
popular than our normal topic of network security:

|
News Reports:
Reuters |
MSNBC |
BBC |
New York Times |
Secure Computing |
News.Com |
Wired |
Boston Globe |
CBC |
FOX news |
Register UK |
Inquirer UK |
Globe and Mail
Update: Nmap 4.21ALPHA4 is now available on the download page. It includes experimental support for the Nmap Scripting Engine.
After a six-month development series with 13 beta releases,
Insecure.Org is pleased to announce the immediate, free availability
of the Nmap Security Scanner version 4.20 from the Nmap download page.
Changes in this release include a second generation OS
detection system, IP option support (source routing, record route,
etc.), an --open option for showing only open ports, version detection
database updates, more detailed XML output, and dozens of bug fixes
and performance enhancements. The full list of changes since 4.11 can be read at the Nmap changelog.
|
Top 100 Security Tools List Released
|
|---|
 After the tremendously successful 2000 and 2003 top security tools
surveys, we are pleased to release our 2006 results at a brand new
site: SecTools.Org. A record 3,243
Nmap users responded this year. Notable trends since 2003 include the
rise in exploitation frameworks such as Metasploit, Impact, and Canvas; the
increased popularity of wireless tools such as Kismet and Aircrack. 44 tools
are new to the list. Security practitioners are encouraged to read the list and investigate tools they
aren't familiar with. You may find the little gem that you never knew
you needed.
After the tremendously successful 2000 and 2003 top security tools
surveys, we are pleased to release our 2006 results at a brand new
site: SecTools.Org. A record 3,243
Nmap users responded this year. Notable trends since 2003 include the
rise in exploitation frameworks such as Metasploit, Impact, and Canvas; the
increased popularity of wireless tools such as Kismet and Aircrack. 44 tools
are new to the list. Security practitioners are encouraged to read the list and investigate tools they
aren't familiar with. You may find the little gem that you never knew
you needed.
English Sectools Coverage:
Digg,
Slashdot,
About.Com,
LinuxSecurity.Com,
SANS ISC,
TAOSecurity,
del.icio.us,
SecuriTeam,
gHacks,
iHacked
International:
Menéame (Spanish),
Kriptopolis (Spanish), ITPro Security (Japanese),
Security.NL (Dutch),
Todo-Linux (Spanish),
CriticalSecurity (Lithuanian),
Xakep (Russian)
|
SecLists.Org Back Up and Running
|
|---|
Our popular SecLists.Org public
mailing list archive is back up and running after it was inexcusably
shut down
with no notice by our soon-to-be-former domain registrar
GoDaddy at the behest of MySpace.Com. We believe web site content is
the responsibility of the site owner (registrant) and (if that fails)
hosting or bandwidth provider. If the whois contact data is valid,
registrars shouldn't be involved without a court order.
News reports and discussion of the shutdown:
CNET News.Com |
Wired |
Wired #2 |
Slashdot |
Digg |
Politech |
Web Host Industry Reviews |
SecurityFocus |
Info World |
Domain Name Wire |
P2PNet |
SecurityPro News |
Digital MediaWire |
SecuriTeam |
Tech Dirt |
Mashable |
SecLog
Update: We have just launched NoDaddy.Com to document GoDaddy's abuses of their registrar status.
After two years of work since the 3.50 release, Insecure.Org is pleased to announce the immediate, free
availability of the Nmap Security Scanner version 4.00 from http://insecure.org/nmap/ .
Changes since version 3.50 include a rewritten (for speed and
memory efficiency) port scanning engine, ARP scanning, a brand new man page and
install guide,
'l33t ASCII art, runtime
interaction, massive version detection
improvements, MAC address spoofing, increased Windows performance, 500 new OS
detection fingerprints, and completion time estimates. Dozens of
other important changes -- and future plans for Nmap -- are listed in the release announcement.
Updates:
Fyodor has given a SecurityFocus interview on 4.00
More English coverage/reviews: Information Security Magazine, Slashdot, Linux Weekly News (LWN), Digg, SANS ISC, OSNews, AllYourTech.Com, LinuxSecurity.Com
International coverage: Heise (German), LinuxFR (French), OpenNET (Russian), derStandard (Austrian), Golem.de (German), Hacking.PL (Polish), WinFuture (German), Kriptopolis (Spanish), Security.NL (Dutch), Tweakers.Net (Dutch), Xakep (Russian)
|
Security List Archive Updated
|
|---|
RSS feeds have been added to all security mailing lists archived at
SecLists.Org, making it even
easier to keep up with the latest news from Nmap-Hackers, Nmap-Dev,
Bugtraq, and all of the others. We have also added Dailydave, a
highly technical discussion list covers vulnerability research,
exploit development, and security events/gossip (with many smart
people participating).
|
NSA Loads Nmap Release Status for President Bush Visit
|
|---|
US President George W. Bush visited the NSA headquarters at Fort
Meade in January 2006. A wall-sized status screen in the background
displays the latest versions of Nmap and some of our other favorite open source tools. Pictures were printed in the
February 6, 2006 edition of Newsweek (article) and the Jan 27 Washington Post (article). The page on the screen is the Talisker Radar. We don't like the NSA tracking our phone calls and email, but they may track Nmap releases all they want.

Loading an external web site on their giant screen was risky. Imagine if this happened (thanks php0t)!
Nmap was also used in a movie named The Listening about NSA spying (details)
Meanwhile, Nmap makes an appearance at Walmart with the Nmap hacking chair
We are proud to announce
that the Nmap man page has been completely rewritten. It is more
comprehensive (double the length) and much better organized than the
previous one. It is meant to serve as a quick-reference to virtually
all Nmap command-line arguments, but you can learn even more about
Nmap by reading it straight through. The 18 sections include Brief
Options Summary, Firewall/IDS
Evasion and Spoofing, Timing
and Performance, Port
Scanning Techniques, Usage
Examples , and much more. It even documents some cool features
that are slated for release in the next Nmap version (runtime
interaction and parallel DNS resolution).
The new man page is best read in HTML format, though you
can alternatively download the Nroff nmap.1 to
install on your system.
We have issued a call for translations of the reference guide, and 29 languages are in progress. See the new documentation page to volunteer or read a translation.
After reading the new man page, you might enjoy the following:
|
Hacker Fiction Books Published
|
|---|

|
Fyodor has co-authored a novel on hacking, along with FX, Joe Grand,
Kevin Mitnick, Ryan Russell, Jay Beale, and several others.
Their individual stories combine to describe a massive electronic
financial heist. While the work is fiction, hacks are described in
depth using real technology such as Nmap, Hping2, OpenSSL, etc. Stealing the Network: How to Own a Continent can be purchased
at Amazon (save $17), and your can read
Fyodor's chapter online for free. STC was a best-seller, ranking for a while as the second-highest selling
computer book on Amazon.
|

|
Update: Syngress has released a sequel: Stealing the Network: How to Own an Identity. They have generously allowed Fyodor to post his favorite chapter for free. So enjoy Bl@ckTo\/\/3r,
by Nmap contributor Brian Hatch. It is full of wry humor and creative
security conundrums to keep the experts entertained, while it also
offers security lessons on the finer points of SSH, SSL, and X Windows
authentication and encryption.
|
| Nmap Gains Advanced Version Detection |
|---|
After several months of intense private development, we are pleased to release Nmap 3.45, including an advanced version detection system. Now instead
of using a simple nmap-services table lookup to determine a port's
likely purpose, Nmap will (if asked) interrogate that TCP or UDP
port to determine what service is really listening. In many cases it
can determine the application name and version number as well.
Obstacles like SSL encryption and Sun RPC are no threat, as Nmap can
connect using OpenSSL (if available) as well as utilizing Nmap's RPC
bruteforcer. IPv6 is also supported. You can read our new version detection paper for the
details and examples, or just download the latest version and try it
out here. Simply add "-sV" to your normal scan
command-line options.
News articles covering Nmap version detection: Slashdot, Hacking Linux Exposed, Security Wire Digest.
| Nmap featured in The Matrix Reloaded |
|---|
We have all seen many movies like Hackers which pass off
ridiculous 3D animated eye-candy scenes as hacking. So I was
shocked to find that Trinity does it properly in The Matrix Reloaded [Under $10 at Amazon].
She whips out Nmap version
2.54BETA25, uses
it to find a vulnerable SSH server, and then proceeds to exploit it
using the SSH1
CRC32 exploit from 2001.
Shame on them for being vulnerable (timing notes). Congratulations to everyone who has helped
make Nmap successful! And thanks to Jason Algol, Titney, Thorsten
Delbrouck, and others for sending pics! Click them for higher-res or see more pics
here.
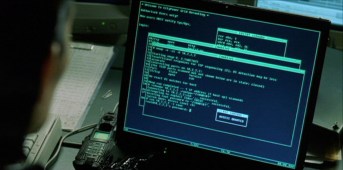
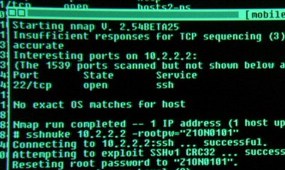
Updates:
- News articles about the Nmap cameo:
BBC,
Slashdot,
SecurityFocus,
Silicon.Com,
Boston
Globe,
CNET
- JWZ has added this cracking scene as an XScreenSaver 4.10 Easter Egg - run 'xmatrix -small -crack'.
- Dave from Lab6
notifies me that Nmap source code is displayed in Battle Royale:
[Screen1]
[Screen2] [Trivia]
- Several people have submitted matrix-themed banners to the propaganda gallery. Feel free to use any of these to link to Insecure.org - we appreciate it!
- The UK's Scotland Yard Computer Crime Unit and the British Computer Society have put out a joint warning
that "Viewers of the new box office blockbuster 'Matrix Reloaded'
should not be tempted to emulate the realistic depiction of computer
hacking." Kids - don't try this at home!
One of the coolest, yet still relatively obscure features of Nmap
is the Idle scan (-sI). Not only does this allow for a completely
blind portscan (no packets sent to the target from your real IP), but
it can even allow you to bypass packet filters in certain
circumstances. Since information on this technique is still rather
scarce, I wrote an informal paper
describing Idle scanning as well as several other exploits based on
predictable IPID sequence numbers. It includes real-life examples as
well as a section on defending yourself from these techniques.
|